Objective
Set up the Glasswall Halo ICAP server to sanitize or block files as they pass through your security infrastructure.
Glasswall Halo’s ICAP Server Integration Guide
- Introduction
- Step 1 - Deploy Glasswall Halo
- Step 2 - Deploy the ICAP server
- Step 3 - Configure your ICAP server client
- Step 4 - Configure the default ICAP profile
- Step 5 - Test by downloading files
Introduction
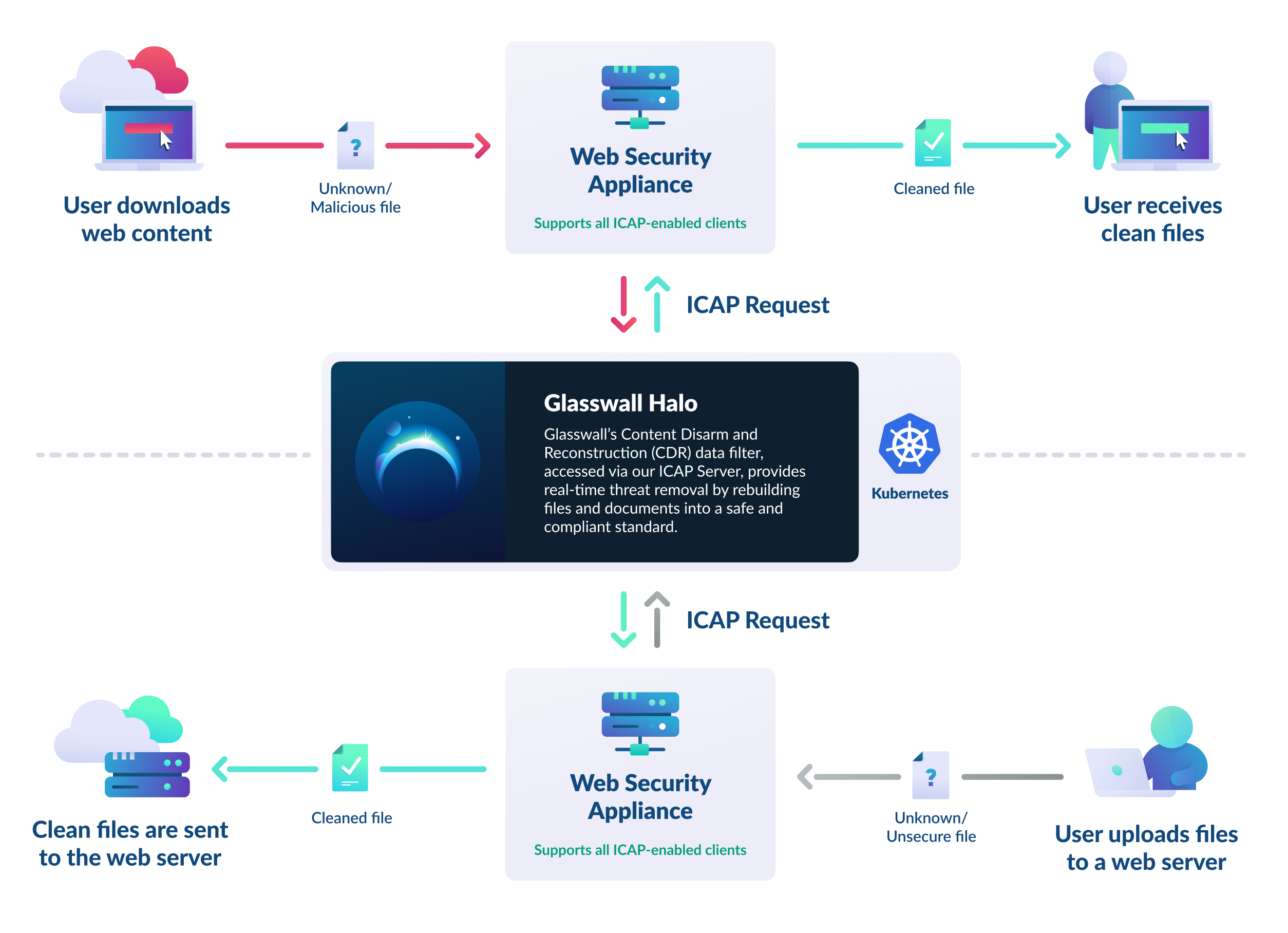
Our ICAP server mediates between ICAP clients (such as proxy servers, firewalls, or gateways) and the Glasswall Halo service. When a file passes through the ICAP client, it is sent to Glasswall Halo for sanitization (CDR) via ICAP before returning to the client.
This ensures complete control of content encountered by members of your organization as they browse the web. You will be able to define the type of files allowed into your organization and what risky content should be sanitized from them to meet your risk profile needs.
What is CDR?
CDR (Content Disarm and Reconstruction) uses a unique method to keep organizations and individuals safe from file-based threats. Instead of trying to detect threats like most cybersecurity solutions, Glasswall CDR follows a 'zero-trust' approach. This means that only files that have been checked and cleaned by Glasswall are considered safe because all potential threats have been removed. We don't try to find malicious code; we simply take away its ability to harm the document.
Learn more about Glasswall CDR
What is ICAP?
The Internet Content Adaptation Protocol (ICAP) is a lightweight protocol designed to enhance transparent proxy servers by offloading tasks like virus scanning and content filtering to dedicated ICAP servers. This allows web servers to focus on HTTP traffic, improving efficiency. ICAP leverages edge devices to deliver specialized services such as ad insertion, content translation, and multi-AV scanning.
Our ICAP server mediates between ICAP clients (such as proxy servers, firewalls, or gateways) and the Glasswall Halo service. When a file passes through the ICAP client, it is sent to Glasswall Halo for sanitization via ICAP before returning to the client.
This ensures complete protection of content traversing your zero-trust boundaries, whether incoming or outgoing from your environments.
Learn more about our ICAP Server
Step 1 - Deploy Glasswall Halo
Before you can begin the ICAP server integration, you’ll need to ensure that Glasswall Halo is deployed and configured. This is because our ICAP server is integrated with Glasswall Halo.
Please refer to our easy-to-follow deployment guides, or skip this step if you’ve already got Halo setup.
Step 2 - Deploy the ICAP server
If you didn't deploy the ICAP server during your Halo deployment, please refer to our step-by-step deployment guide.
Step 3 - Configure your ICAP server client
After the ICAP server is operational, you'll need to configure your ICAP client to route its requests through the server. Our ICAP server is compatible with any ICAP-enabled web security appliance.
For additional support, please see our integration guides for popular clients and our proxy configuration guides for help setting up proxy environments.
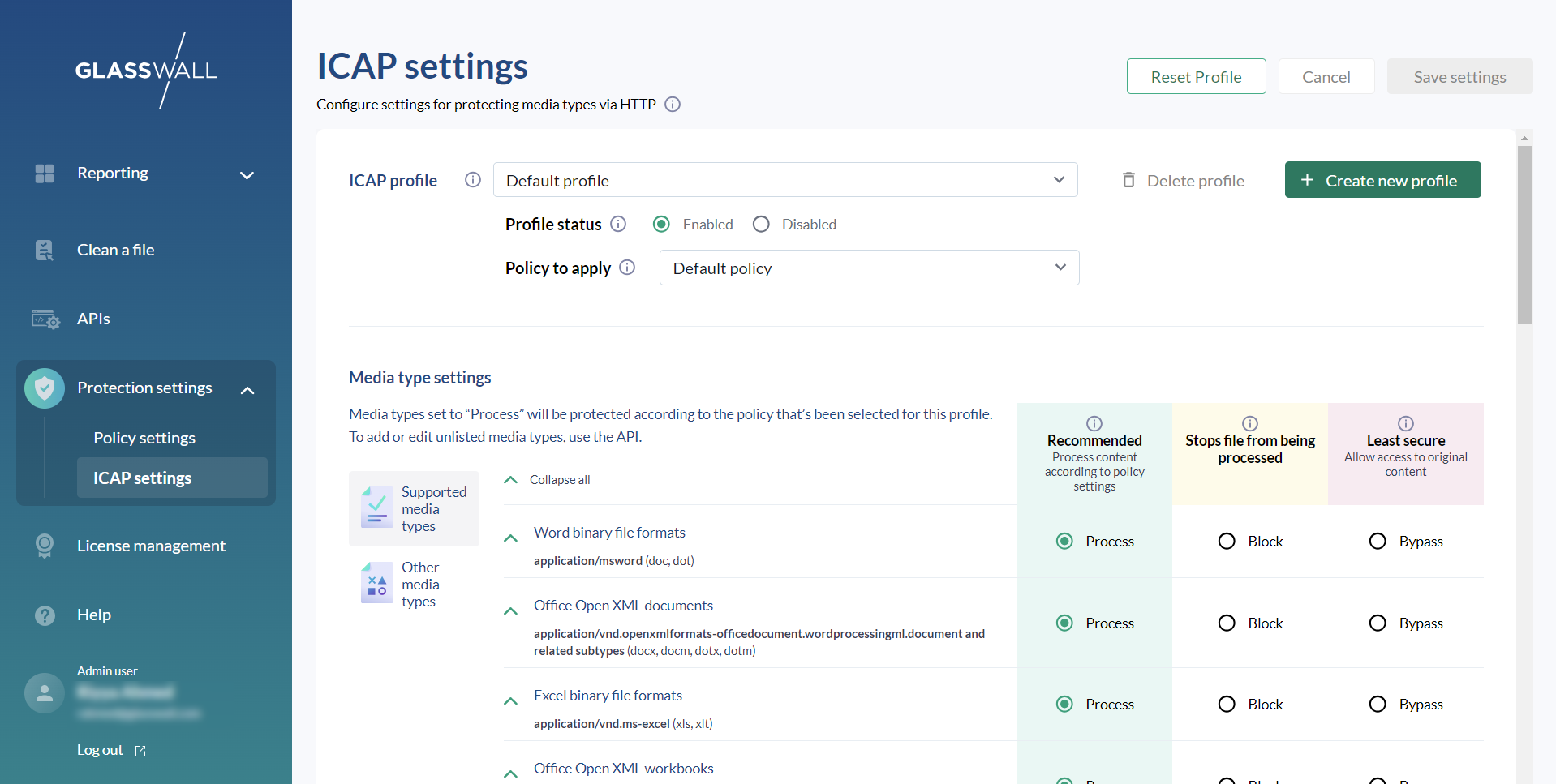
Step 4 - Configure the default ICAP profile
Next, we'll set up the default ICAP profile to manage how different file types are handled. ICAP server requests use a content type known as Media Types, which can be tricky to interpret.
To make it easier, we've matched these media types to the file types supported by Glasswall Halo and other common formats - please refer to the Supported Media Types for more information.
Note: you can create multiple ICAP profiles and assign one to each ICAP request. If none is specified, this default profile will be used.
- Configure the ICAP profile through the ICAP Profile Management API endpoint or directly via Halo’s ICAP settings.
- For each mapped file type, you can define what action the ICAP server should take.
- Here, we'll process Word, Excel, and PowerPoint files, block PDFs, and bypass all other file types.
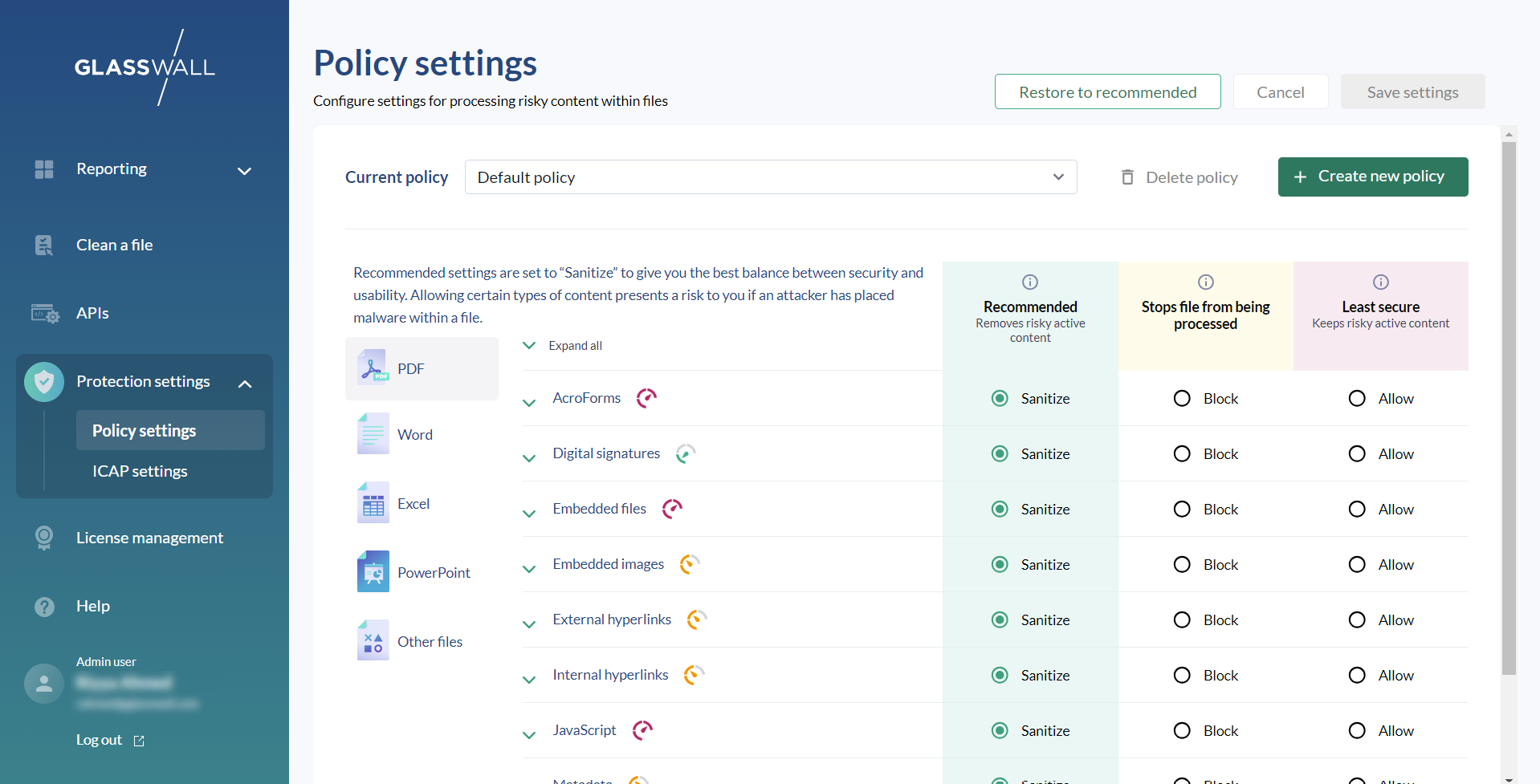
- Next, configure your Policy settings.
- You may leave Glasswall's default content management policy which sanitizes all risky content from processed files to ensure maximum protection or amend them as required.
Step 5 - Test by downloading files
You're now ready to browse securely.
- To test the file sanitization, download a Word, Excel, or PowerPoint file.
- As the file downloads, your web security appliance will intercept it and send it to Glasswall Halo via ICAP. Here it is sanitized in under a second with no noticeable change in user experience.
Error Handling
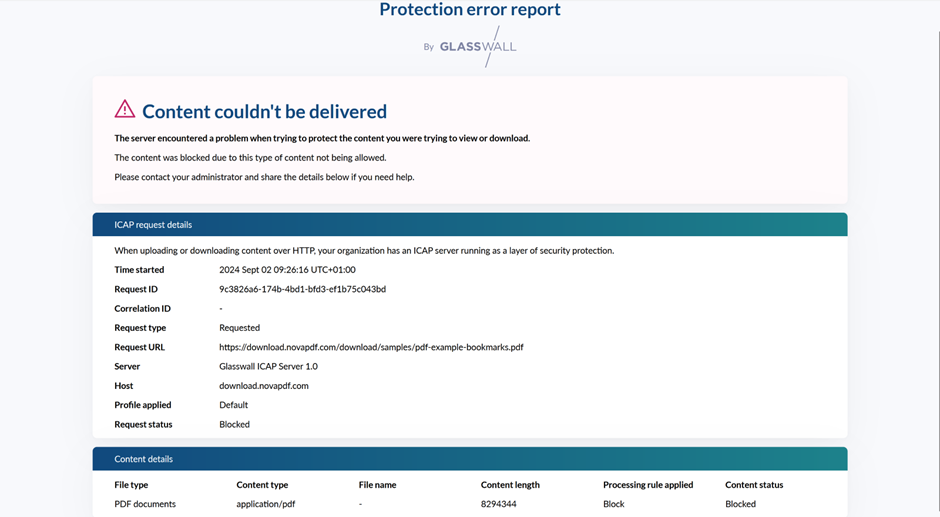
- Since PDFs are set to be blocked by this default profile, test it by trying to view or download a PDF.
- The file should be replaced with a Halo protection report explaining why the content is unavailable, preventing the potentially dangerous file from reaching the user.
Conclusion
With all steps completed, your ICAP server is now ready to handle and sanitize files using Glasswall Halo’s Content Disarm and Reconstruction (CDR) process. The ICAP server mediates between clients and Glasswall Halo, enforcing security policies, automating file handling, and enhancing protection while ensuring minimal disruption to user experience.