As an alternative to cloud managed Kubernetes deployments, Glasswall Halo can also be deployed via a single-node configuration into traditional Virtual Machine infrastructure. This is an option for deployment to on-premise environments where utilisation of cloud infrastructure is not possible.
Single-node deployments comprises of three main components (for version information, please see our Release Notes):
- Red Hat Enterprise Linux base operating system
- Rancher Kubernetes Engine Government (RKE2) - a Cloud Native Computing Foundation (CNCF) certified Kubernetes distribution
- Glasswall Halo Helm charts and container images
To simplify deployment of the above components, preconfigured VM images are available in OVA and VHD image formats.
Architecture
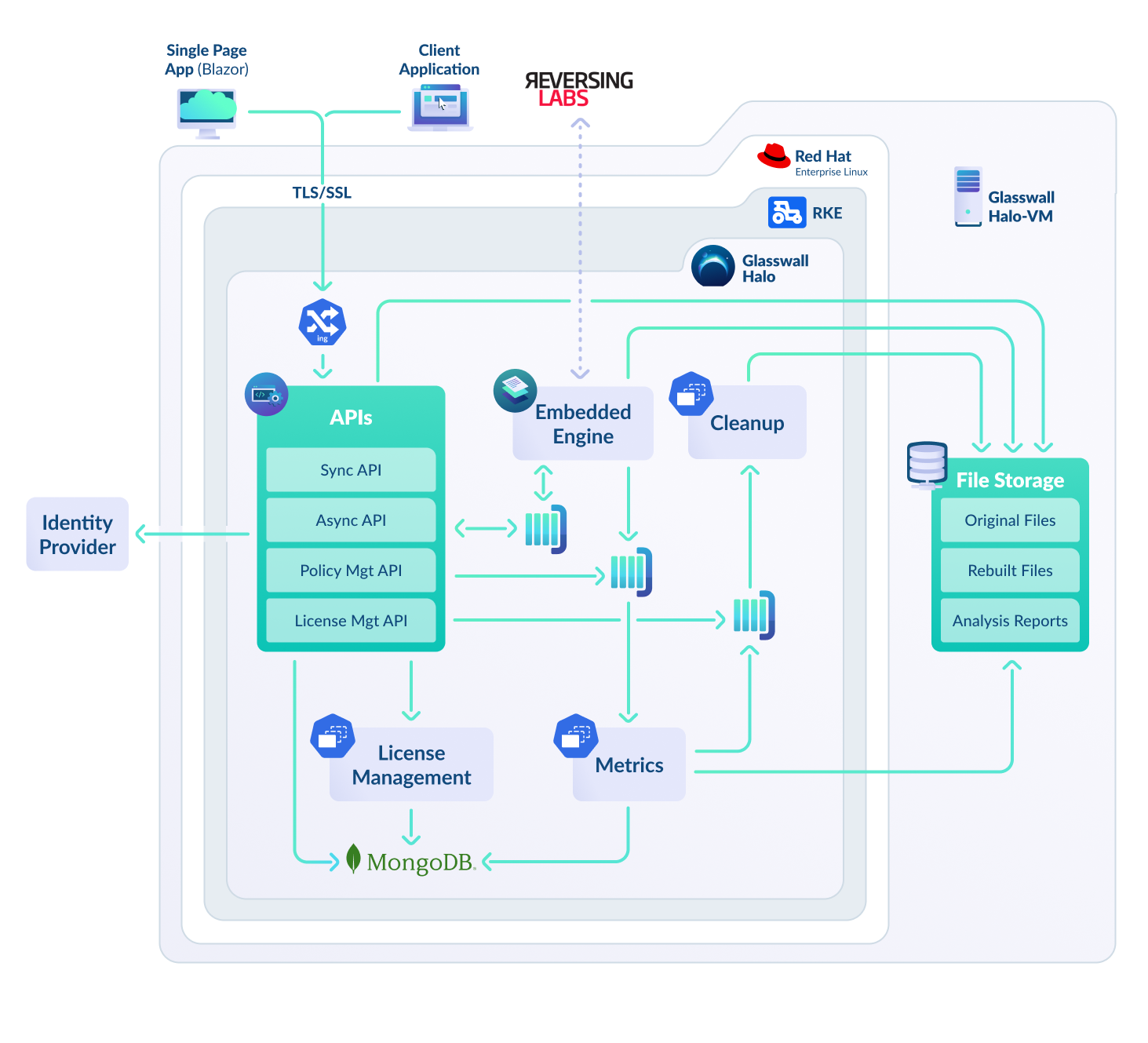
Security Posture
The following security hardening procedures have been carried out for each of the main components of the VM deployments:
- Hardened Red Hat Enterprise Linux base operating system
- Hardening utilises the DoD Security Technical Implementation Guides (STIGs) for Red Hat Enterprise Linux
- Rancher Kubernetes Engine Government (RKE2)
- Hardening utilises the Center for Internet Security (CIS) Kubernetes configuration for RKE2
- Glasswall Halo Helm Charts and Container Images
- As per the standard Glasswall Halo deployments, all charts and images are subject to continual SCA, SAST, DAST, IaC and container scanning and associated patching.
Security reports from the above procedures are available on request.
Current Limitations of Single-Node VM Deployments
When deploying in the single node configuration, scalability is limited to the size of the target VM. The Single-Node deployment will dynamically allocate the correct number of engines based on the avaliable resources of the underlying VM.