
Providers
Settings are specific to service providers. Use the provided connection profiles.
Note - All connection profiles are available through the *Preferences → Profiles* tab.
Connecting
If you have access to a server using a secure shell (SSH2), most probably sftp-server is also installed and configured and you can connect using SFTP.
OpenSSH Configuration Interoperability
Public Key Fingerprints
Public key fingerprints are checked against and written to ~/ssh/known_hosts when accepted. This does not apply to the Mac App Store version which does store key fingerprints in the preferences.
Configuration File
The following configuration options from ~/.ssh/config are supported for SFTP connections:
- IdentityFile for public key authentication.
- IdentityAgent for public key authentication. Specifies the UNIX-domain socket used to communicate with the authentication agent.
- HostName aliases.
- User preference for login credentials.
- ProxyJump to connect via SSH tunnel through bastion server.
- PreferredAuthentications to limit authentication methods tried to login.
- IdentitiesOnly. Only try explicitly set private keys to authenticate but not all identities found in SSH agent. Resolves Too many authentication failures errors with servers limiting the number of attempted authentication requests.
- A bookmark will update its public key authentication setting from the IdentityFile configuration in
~/.ssh/config. Also when opening a new connection using File → Open Connection…, IdentityFile and User parameters in the OpenSSH user config file are auto completed.
Example ~/.ssh/config configuration:
Host myhostname
User myusername
IdentityFile ~/.ssh/mykey-rsa
To use the same key for all hosts add a wildcard entry such as
Host *
IdentityFile ~/.ssh/mykey-rsa
which is then used when configuring a new bookmark.
Important - If you have a configuration in your ~/.ssh/config make sure to specify the Host alias as hostname in your bookmark configuration. This is important for cases the `Host` alias is different from the HostName:
Host myhostalias
HostName myverylonghostname.exmaple.com
User myusername
IdentityFile ~/.ssh/mykey-rsa.pub
For the configuration above the hostname to specify in your bookmark is myhostalias.
Default Public Key Authentication Keys
You can enable the use of a default set of keys ~/.ssh/id_rsa and ~/.ssh/id_dsa (in this order) by setting the hidden configuration option ssh.authentication.publickey.default.enable to true.
defaults write ch.sudo.cyberduck ssh.authentication.publickey.default.enable true
Public Key Authentication
Public-key authentication allows you to connect to a remote server without sending your password over the Internet. Public-key authentication uses two keys:
- a private key that only you have that should be kept in a secure place and protected with a password
- the public key, which is placed on the server you wish to gain access to, usually by the system administrator when your account is set up.
Private keys can be configured in the Bookmark or Connection panel.
PuTTY Key Format Interoperability
PuTTY private keys (.ppk) are supported for rsa key types. ed25519 is not supported.
OpenSSH Key Format Interoperability
OpenSSH private keys of type rsa, dsa, ecdsa and ed25519 (in OpenSSLPEM format) are supported. The new OpenSSH format (openssh-key-v1) is only supported for ecdsa and ed25519.
Configure Public Key Authentication
- Run the command
ssh-keygenfrom the Terminal.app (macOS) or console (Windows) to generate a public/private pair of keys. They will be put in your directory~/.ssh, though you will probably be asked to approve or change this location. When you generate the keys you will be asked for a 'passphrase'. If you use a passphrase then you will have to enter it each time you use the keys for authentication. That is, you will have to type in the passphrase every time you log in, just as you would with a password. If you don't enter a passphrase (just press the return key) then you will be allowed to log in without having to enter a passphrase. This can be more convenient, but it is less secure.ssh-keygen -m PEM -t rsa - Copy the public key to the remote host you wish to access and add it to the file
authorized_keysin your~/.sshdirectory. (If that file does not exist then you should create it.) Anybody listed in the authorized_keys file (via their public key) is allowed to log-in, provided that they can prove that they possess the corresponding private key. Thus, if you have the private key in your .ssh directory on your home machine you'll be allowed in.ssh hostname < ~/.ssh/id_rsa.pub 'cat >> .ssh/authorized_keys' - In the Connection Dialog or the Bookmark editor in Cyberduck select Use Public Key Authentication and select the private key in your
.sshdirectory.
CA signed SSH Certificate Interoperability
Certification Authority (CA) sigend SSH certificates are supported for keys of type rsa, dsa, ecdsa, and ed25519.
Public Key Authentication Using SSH Agent
When connecting to a SSH server, Cyberduck will lookup matching private keys from the SSH agent when attempting to authenticate with the server if no password is available and no explicit private key to use is configured in the bookmark.
The following agents are supported:
* [Pageant](https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html). Refer to [How To Use Pageant to Streamline SSH Key Authentication with PuTTY](https://www.digitalocean.com/community/tutorials/how-to-use-pageant-to-streamline-ssh-key-authentication-with-putty).
* OpenSSH for Windows using the pipe (`\\.\pipe\openssh-ssh-agent`) by default. Use `IdentityAgent` to set a custom socket path for any other compatible agent if needed.
Tip - When authenticating using Public Key Authentication with an SSH agent containing multiple identities, it makes sense to add `IdentitiesOnly yes` in `~/.ssh/config` to limit authentication attempts with this identity only. Otherwise the server may deny the connection because of too many login failures and you will recieve the error _Too many authentication failures_.
Since the private key is not always available on the filesystem, specifying a public key as IdentifyFile is also supported. This can be used to authenticate using an SSH agent backed by a hardware token containing the private key for example.
Example ~/.ssh/config configuration:
Host myhostname
User myusername
IdentityFile ~/.ssh/mykey-rsa.pub
IdentitiesOnly yes
One-Time Passcodes (2FA)
Using a challenge-response authentication with one-time password generators such as DUO, SecurID or Google Authenticator is supported. After the initial login prompt for the username and password, a second login prompt is displayed to enter the one-time passcode.
Google Authenticator
A setup with a two-step verification such as Google Authenticator is supported.
Use the following configuration steps:
- Install
libpam-google-authenticatoron the server. - Run
google-authenticatorto create a new account and scan the 2D barcode using the Authenticator application on your phone. Refer to Install Google Authenticator. - Make it required for SSH logins by running
echo 'auth required pam_google_authenticator.so' >> /etc/pam.d/sshd. - Add
ChallengeResponseAuthentication yesto/etc/ssh/sshd_configwithecho 'ChallengeResponseAuthentication yes' >> /etc/ssh/sshd_config.
When logging in, enter the time-based token requested after providing username and password.
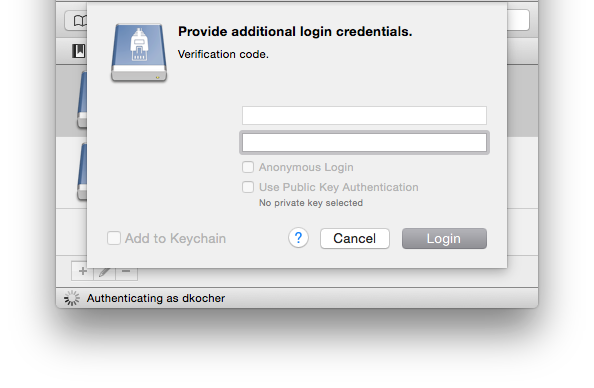
Verify Host Keys
Upon connecting to an SSH server for the first time, you will see a message to verify the host key uniquely identifying the server. You can ask your provider for the public fingerprint of the server to make sure you are connecting to the right host. Subsequent connections to the SSH server will make sure that the host key does not have changed to prevent spoofing attacks.
Connect via SSH Tunnel Through Bastion Server
Using the ProxyJump configuration directive in ~/.ssh/config you can connect through a tunnel. The bookmark configuration refers to the target host in the internal network. We should find a ProxyJump directive in the OpenSSH configuration ~/.ssh/config matching the hostname in the bookmark.
Sample configuration:
Host internal
HostName server.lan
ProxyJump user-external@jump.example.org:2222
User user-internal
You can also work with aliases like
Host bastion-host-nickname
HostName bastion-hostname
User username
Port 2222
Host remote-host-nickname
HostName remote-hostname
ProxyJump bastion-host-nickname
Open in Terminal
Open in Terminal allows you to open an SSH shell for the current working directory with a single click.
Warning - The feature is not supported when running Cyberduck from the Mac App Store because of [sandboxing restrictions](https://github.com/iterate-ch/cyberduck/issues/7664).
Disable WSL
There is a hidden configuration option for toggling additional SSH-terminal applications. Currently implemented are ssh.exe (OpenSSH built-in to Windows 10 since version 1709), bash.exe (using WSL and invoking ssh there) as well as PuTTY.
- Disabling OpenSSH:
terminal.openssh.enable=false - Disabling WSL:
terminal.windowssubsystemlinux.enable=false
PuTTY.exe
Use View → Customize Toolbar... to add the Open in Putty toolbar icon to your browser.
Location of the PuTTY installation:
By default, the executable putty.exe must be located in your user home folder. You can change the install location by editing the hidden configuration option terminal.command.ssh to point to the path of the executable.
Distribution (CDN)
You can enable custom origin Amazon CloudFront (Content Delivery Network) distribution using File → Info → Distribution (CDN).
Create and Expand ZIP or TAR Archives
The remote systems must have the archiving tools tar or zip installed respectively. Use View → Customize Toolbar... to add the Archive toolbar button to your browser window. It is not included in the default toolbar configuration.
Note - _Send custom commands_ and _Create and expand ZIP/TAR Archives_ are limited to FTP and SFTP.
Preferences
Default Protocol Handler
You can set Cyberduck or a third-party application as the default application (protocol handler) for SFTP in Preferences → SFTP. When you click URLs in another application like your web browser, this application is opened to open the URL instead.
Supported Algorithms
Ciphers
aes{128,192,256}-{cbc,ctr}, blowfish-{cbc,ctr}, 3des-{cbc,ctr}, twofish{128,192,256}-{cbc,ctr}, twofish-cbc, serpent{128,192,256}-{cbc,ctr}, idea-{cbc,ctr}, cast128-{cbc,ctr}, arcfour, arcfour{128,256}, aes{128,256}-gcm@openssh.com, chacha20-poly1305@openssh.com
Key Exchange
diffie-hellman-group1-sha1, diffie-hellman-group14-sha1, diffie-hellman-group14-sha256, diffie-hellman-group15-sha512, diffie-hellman-group16-sha512, diffie-hellman-group17-sha512, diffie-hellman-group18-sha512 diffie-hellman-group-exchange-sha1, diffie-hellman-group-exchange-sha256, ecdh-sha2-nistp256, ecdh-sha2-nistp384, ecdh-sha2-nistp521, curve25519-sha256@libssh.org
Signatures
ssh-rsa, ssh-dss, ecdsa-sha2-nistp256, ecdsa-sha2-nistp384, ecdsa-sha2-nistp521, ssh-ed25519
Compression
Compression with zlib and zlib@openssh.com is supported.
Private Key Files
pkcs5, pkcs8, openssh-key-v1, ssh-rsa-cert-v01@openssh.com, ssh-dsa-cert-v01@openssh.com
Incompatibilities
Serv-U MFT
Serv-U MFT does not fully implement SFTPv3. Files cannot be created, renamed, uploaded as a required flag is not implemented and results in error messages.
Known Issues
Too many authentication failures
Running an SSH agent with many added identities can lead to the server error Too many authentication failures when trying to authenticate with all available identities.
- Select the identity in the bookmark_ with SSH Private Key.
- Increase the allowed authentication tries on the server by adjusting
MaxAuthTries.
Possible remedies using configuration in OpenSSH configuration file:
IdentitiesOnlyin client configuration file~/.ssh/config. Only try to authenticate with explicitly set private key instead of all identities retrieved from SSH agent.- Set
PreferredAuthenticationsin client configuration file~/.ssh/configto disable public key authentication for example.
Illegal sftp packet length. Invalid packet: indicated length 1114795883 too large
The error message Invalid packet: indicated length 1114795883 too large may indicate you have either:
- An
echostatement in your shell init script like .bashrc. Make sure it does not output any text. - Interoperability issue with Globalscape EFT Server (Issue #5308).
- Possibly the server is printing a message similar to Please login as the ubuntu user rather than root user. Please verify the username for your connection.
- Enable SSH access on your server. Use the sftp command in a terminal to verify
sftp username@domain_name. It'll ask for your password. If you don't have SSH access, you'll get "Received message too long", hence the error message.
Kex Timeout
This error can occur if you are connecting the first time to a device with a slow processor. You can raise the tmeout value in Preferences → Connection → Timeout.
Connect Does not Work
Cyberduck refuses to connect if there are malformed entries in your known_hosts file located under ~/.ssh. Renaming this file and recreating it usually resolves this. An alternative requires manually editing the known_hosts file removing all malformed entries. Please refer to sshd(8) for a valid format.
Symbolic Link isn't Accessible
Symbolic links only work within Glasswall Meteor Connect if the target of the symbolic link is available within the mounted path.
Free Space Calculation is Incorrect
The available space for a volume mounted over SFTP is determined using quota features of the SSH protocol. Technically using the space-available extension of the SFTP protocol or the statvfs@openssh.com extension from OpenSSH. If the connected device returns an invalid value (e.g. from the disk the server is running instead of the data disk) you will get an incorrect calculation for the free space.
You can work around the issue using one of the following options:
- Set a default path you want to connect to within the bookmark Path option.
- Disable the feature within Glasswall Meteor Connect by setting the hidden property
fs.quota.enable=falsein %AppData%\glasswallmeteorconnect\default.properties on Windows.