Overview
This guide provides step-by-step instructions for integrating Keycloak Single Sign-On (SSO) with the Glasswall Halo platform in an offline (air-gapped), on-premises environment.
It assumes you’ve already deployed the Single Node Halo platform (e.g., on VMs via Proxmox or ESXi) and now want to enable OIDC-based SSO using Keycloak.
You’ll learn how to:
- Set up a Keycloak server with HTTPS in an offline environment (using a preloaded container image or manual VM installation).
- Import and customize the provided
glasswall-realm.jsonKeycloak configuration. - Configure TLS certificates and DNS/host resolution for both Keycloak and Halo.
- Deploy the Halo Portal and related services:
cdrplatform-portalcdrplatform-portalaccesscdrplatform-api-access
Glasswall Halo's Keycloak SSO Integration Guide
- Prerequisites
- Step 1 - Configuring Keycloak for Glasswall Halo SSO
- Step 2 - TLS Certificates and DNS Considerations
- Step 3 - Deploying Halo Services with Keycloak SSO (Helm Configurations)
- Step 4 - Validation and Testing SSO Integration
- Step 5 - Troubleshooting
Prerequisites
Environment Requirements
- This setup is intended for air-gapped or strictly on-premises environments.
- The Single Node Halo cluster must already be deployed.
- Internal DNS resolution must be in place, either via a local DNS server or manually through
/etc/hostsentries. - Keycloak must be installed locally on a host or virtual machine.
→ Keycloak Documentation & Installation
Required Resources
- A pre-configured realm file (
glasswall-realm.json), provided by Glasswall Support. - Local access to Halo Helm charts for deployment within the Single Node Halo cluster.
DNS / Hosts configuration
Ensure the hostname for your Keycloak server is resolvable by both client machines and Halo platform components.
- With internal DNS: Create an A record for
keycloak.dev.localpointing to the Keycloak server’s IP address. - Without internal DNS: Add the following entry to the
hostsfile on each machine that needs access:
Step 1 - Configuring Keycloak for Glasswall Halo SSO
Glasswall provides a Keycloak realm configuration (as a JSON file) that defines the realm, clients, roles, and scopes needed for Halo's SSO.
You can import this configuration to avoid manual setup. In an offline setup, do this via the Keycloak Admin UI.
1.1 - Importing the Glasswall realm configuration
a. Obtain the realm export: You should have a file named glasswall-realm.json. This file contains the realm settings for Halo's SSO.
Glasswall realm summary
The Glasswall realm includes the following preconfigured items:
-
Realm ID: glasswall
-
Clients
- halo-portal-client
- halo-api-access
- halo-portal-access
-
Key roles
- Realm-level: Admin, User
- Client-level: Halo client Admin and User roles.
- Client Scopes (pre-configured with mappers):
- PortalUserScope: Necessary claims (roles, email) to tokens.
-
Token lifespan
- SSO Session Idle Timeout: 30 mins
-
Authentication: Standard username/password.
b. Log into Keycloak admin
- Using a web browser, navigate to the Keycloak admin console at https://<KEYCLOAK_HOST>:8443/ and log in with the master admin account.
c. Import the realm.
- In the admin console select the dropdown that currently shows "Master" and click Create Realm.
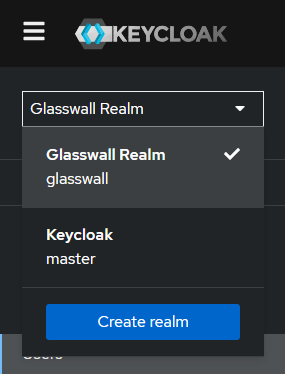
- From the Create Realm screen, select Import, and upload the
glasswall-realm.jsonfile.
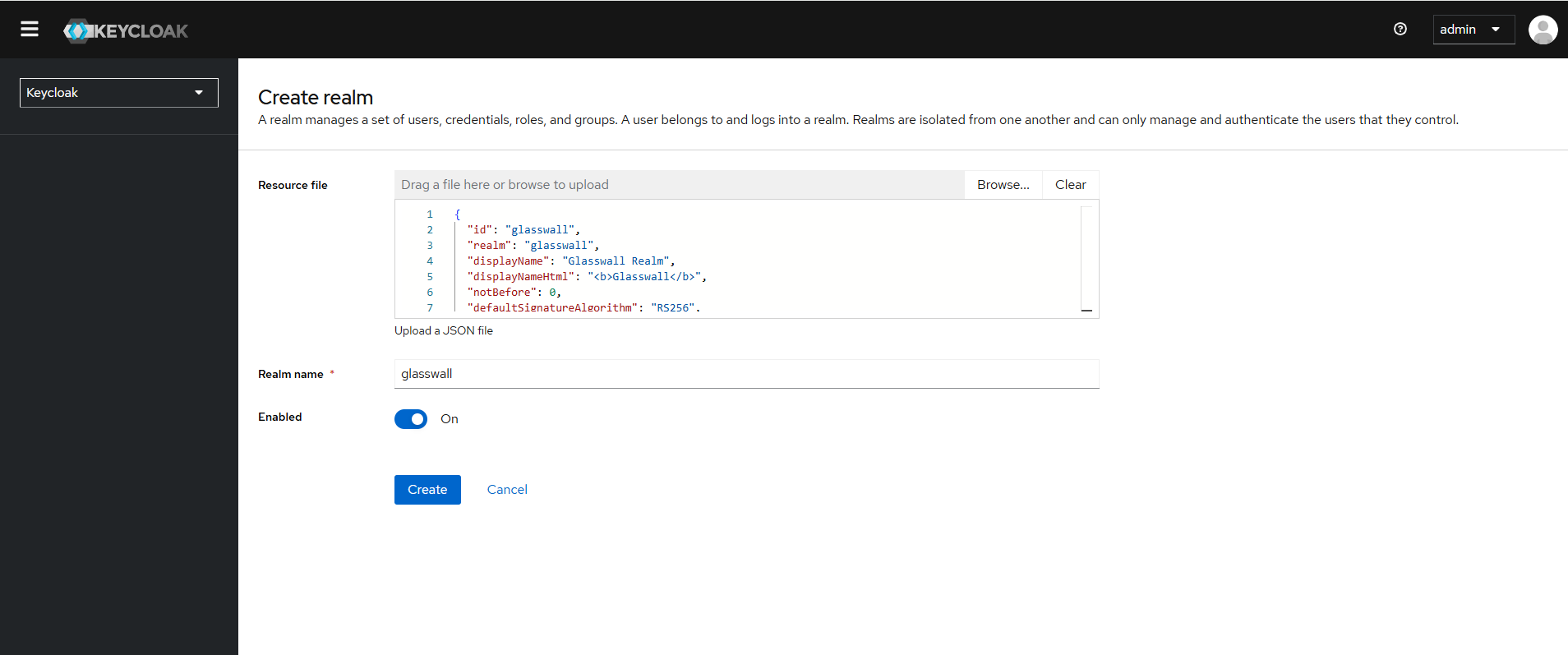
- Keycloak will parse the file and populate the realm name (e.g.,
glasswall).- Confirm the import.
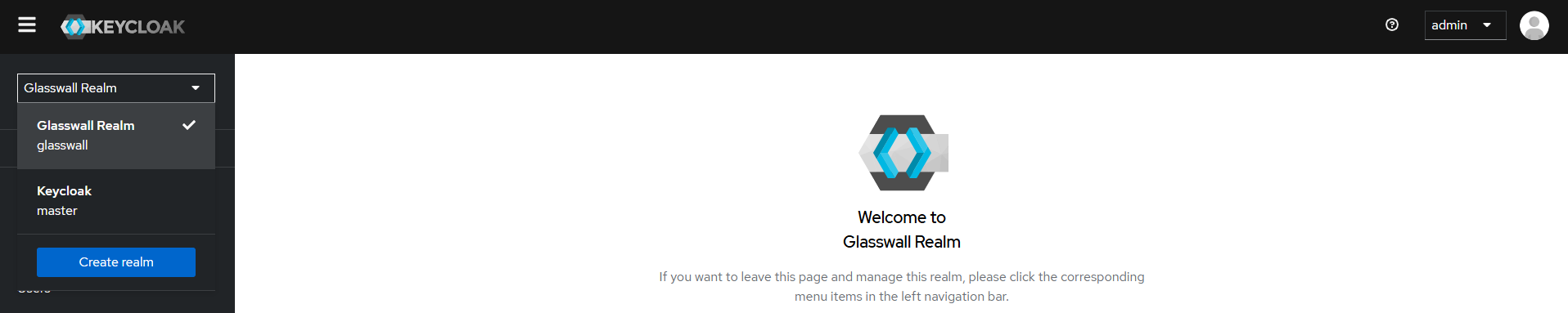
d. Verify realm settings
- After import, review key settings and ensure:
- Realm name is
glasswall. - Realm is enabled.
- SSL Required: likely set to
external. - Clients should include:
halo-portal-clienthalo-portal-accesshalo-api-access
- Realm name is
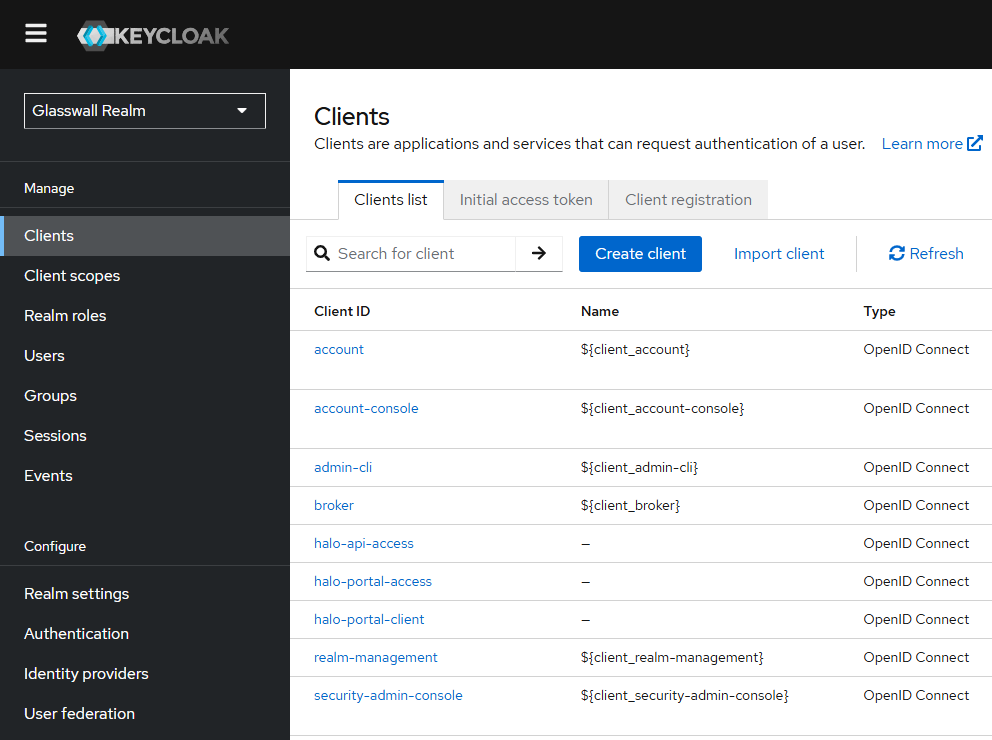
1.2 Customizing client settings (hostnames and redirect URIs)
Next, for each of the Halo clients, update the configuration to match your environment.
halo-portal-client (Portal frontend)
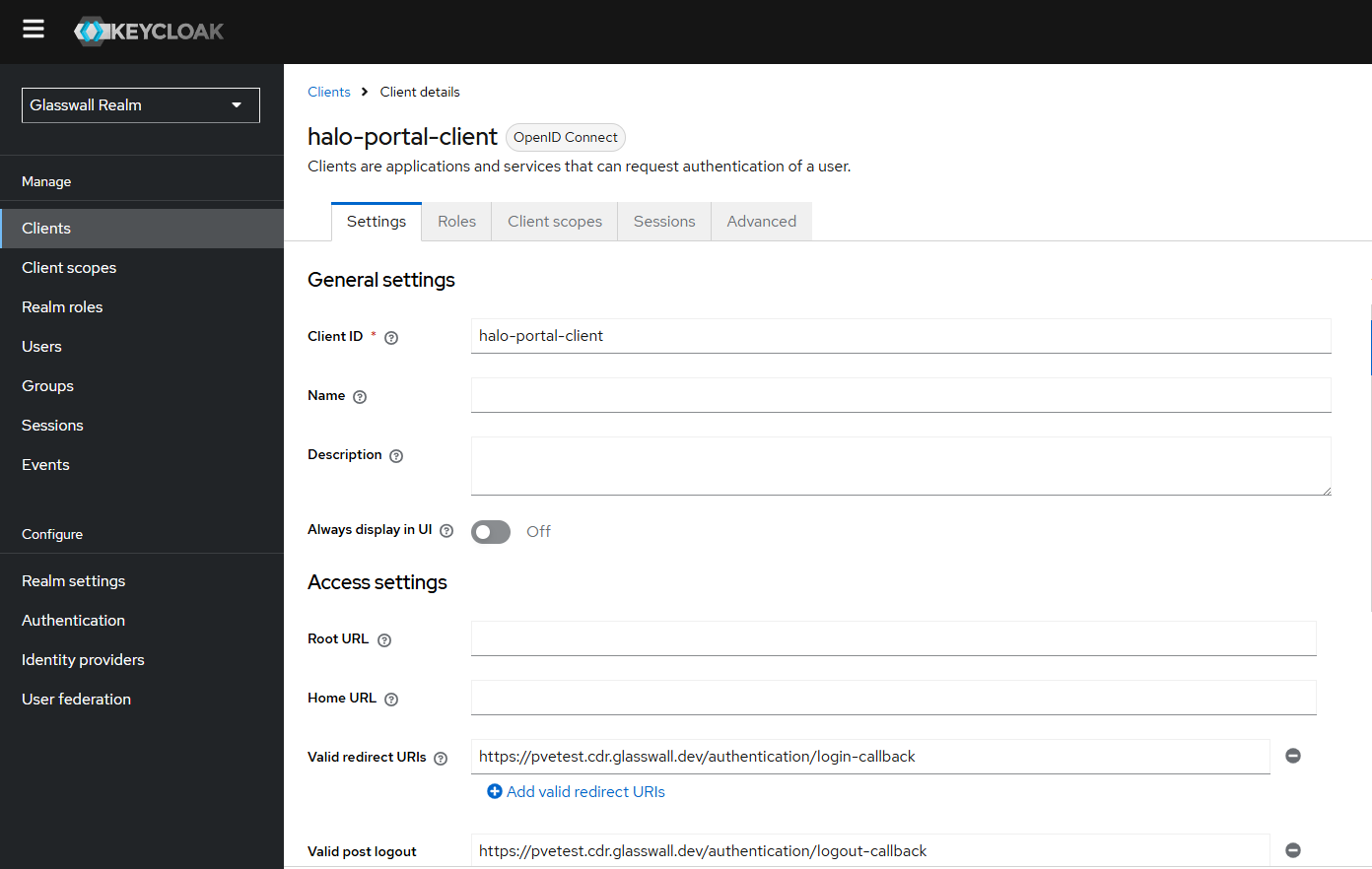
Valid redirect URIs: Replace the placeholder domain in the realm JSON with your actual portal domain. The sample configuration uses a test domain (for example, https://pvetest.cdr.glasswall.dev/authentication/login-callback). Update this value to match the URL users will use to access your Halo portal.
For instance, if your Halo portal is available at https://halo.dev.local/ and the application’s login callback path is /authentication/login-callback, set:
- Valid redirect URIs:
https://halo.dev.local/authentication/* - Web Origins:
https://halo.dev.local - Root URL (optional):
https://halo.dev.local - Valid post logout Redirect URIs:
https://halo.dev.local/authentication/logout-callback
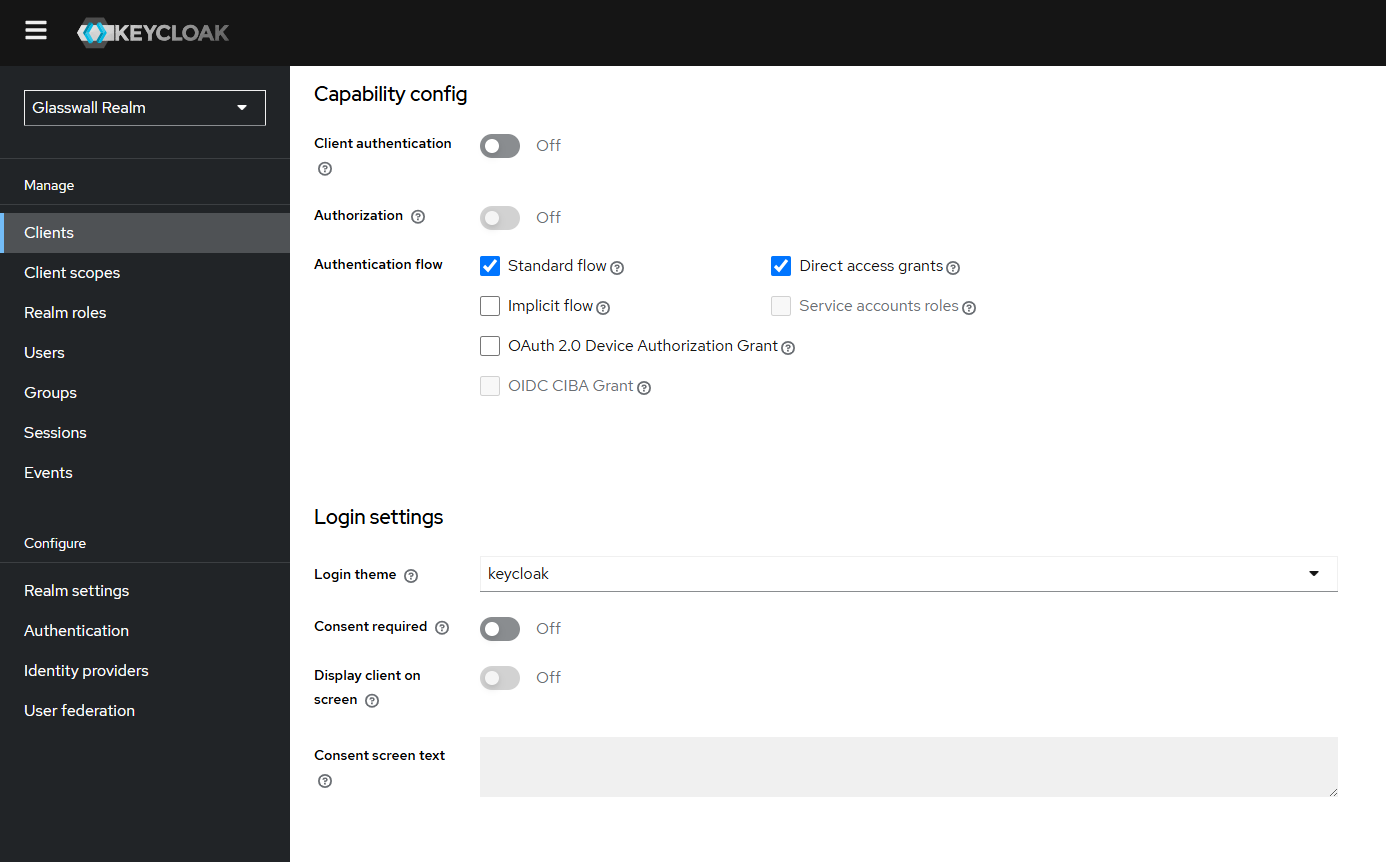
halo-portal-access (Portal backend)
- Valid redirect URIs: (e.g.,
https://pvetest.cdr.glasswall.dev/*)- Update it to your portal domain.
- Web Origins:
https://halo.dev.local
halo-api-access
- Leave redirect settings as-is, and save each client’s settings.
1.3 Creating users and assigning roles
Now you'll create users and assign Halo roles.
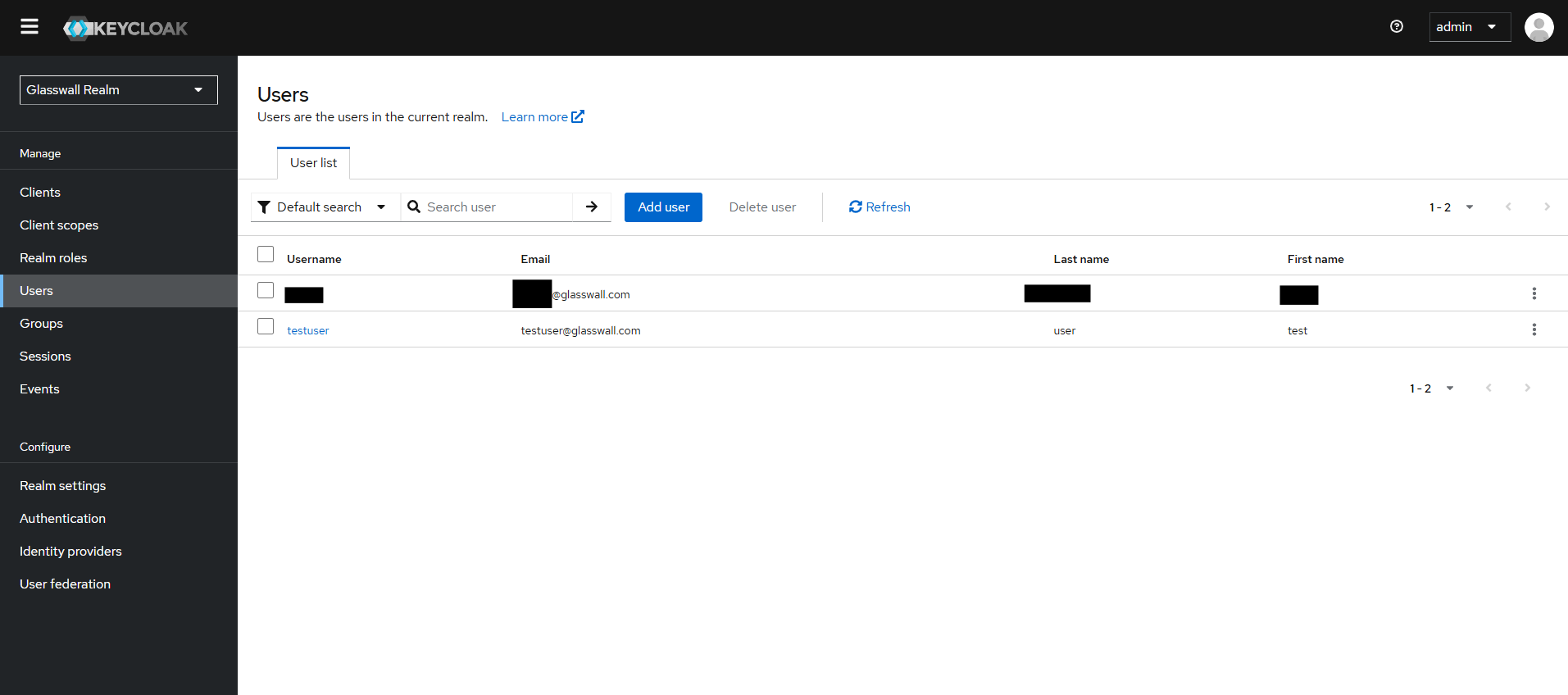
a. In the glasswall realm, navigate to Users → Add User.
b. Fill in the username and details.
c. In Credentials section, set a password and uncheck "Temporary".
d. In Role Mappings, assign:
- Realm roles:
AdminUser
- Client roles:
halo-portal-client[admin, user]halo-api-access[admin, user]halo-portal-access[admin, user]
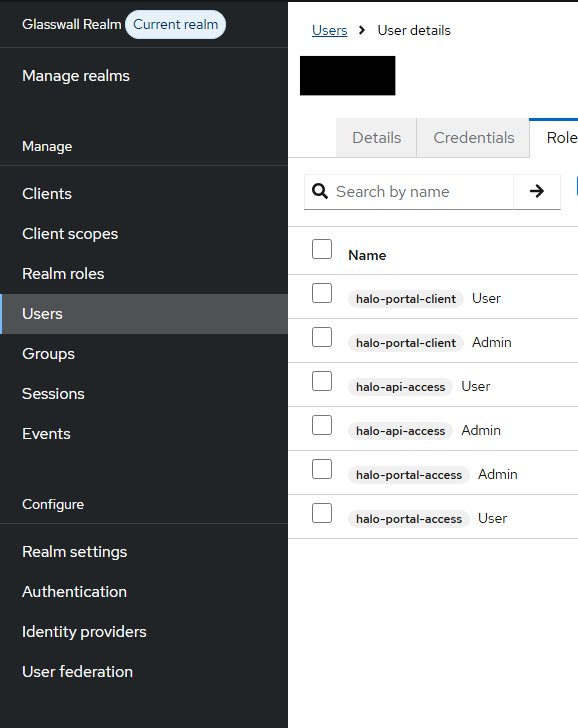
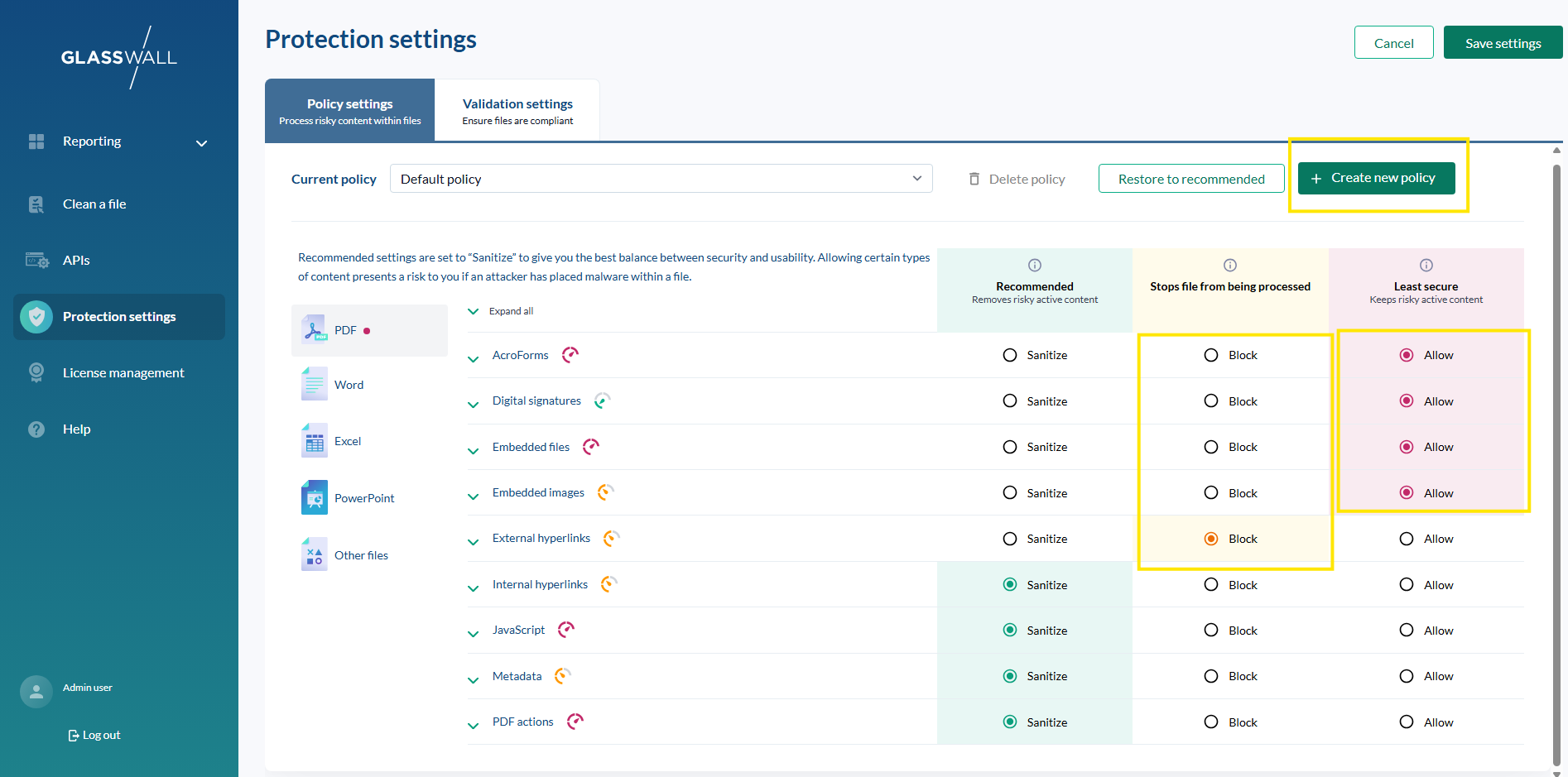
An Admin user sees:
And can manage:
Including:
Step 2 - TLS certificates and DNS considerations
Ensure proper TLS trust and DNS for all components.
2.1 TLS Trust
Halo platform services (Portal, Portal-Access, API-Access) must trust Keycloak’s certificate.
2.2 DNS and /etc/hosts
Ensure:
- Keycloak hostname resolves for all services and users
- Halo domains resolve as well
Step 3 - Deploying Halo services with Keycloak SSO (Helm configurations)
Halo is deployed via Helm; offline environments use charts bundled with the system.
Deploy Halo Portal
portal_image_tag=$(k get deploy portal -o json | jq -r '.spec.template.spec.containers[0].image' | cut -d":" -f2)
portal_domain="glasswall.example.com"
keycloak_domain="keycloak.example.com"
helm upgrade --install cdrplatform-portal ./cdrplatform-portal \
--set image.tag="${portal_image_tag:?}" \
--set image.pullPolicy=IfNotPresent \
--set ingress.tls.enabled=true \
--set ingress.tls.domain="${portal_domain:?}" \
--set ingress.tls.secretName="tls-secret" \
--set configuration.BackendUrl="https://${portal_domain:?}" \
--set configuration.HaloVersion="2.12.0" \
--set configuration.EnabledPages="SystemSettings\,PolicySettings\,ValidationSettings" \
--set configuration.OIDC.ProviderOptions.Authority="https://${keycloak_domain:?}/realms/glasswall" \
--set configuration.OIDC.ProviderOptions.ClientId="halo-portal-client" \
--set configuration.OIDC.ProviderOptions.RedirectUri="https://${portal_domain:?}/authentication/login-callback" \
--set configuration.OIDC.ProviderOptions.PostLogoutRedirectUri="https://${portal_domain:?}/authentication/logout-callback" \
--set configuration.OIDC.ProviderOptions.Scope="openid profile api://cdrplatform-portal-access/PortalUserScope" \
--set configuration.OIDC.ProviderOptions.SilentCheckSsoRedirectUri="https://${portal_domain:?}/silent-check-sso.html" \
--set appenvironment.HTTP_CSP_FRAME_SRC="'self' https://${keycloak_domain:?} https://${portal_domain:?}/silent-check-sso.html" \
--set appenvironment.HTTP_CSP_CONNECT_SRC="'self' https://${keycloak_domain:?}" \
--set configuration.Authentication__Schemes__Bearer__RequireHttpsMetadata=true \
--set configuration.Authentication__Schemes__Bearer__MetadataAddress="https://${keycloak_domain:?}/realms/glasswall/.well-known/openid-configuration" \
--set configuration.Logging__LogLevel__Keycloak="Debug" \
--atomic
Deploy Portal-Access
image_tag=$(k get deploy portal-access -o json | jq -r '.spec.template.spec.containers[0].image' | cut -d":" -f2)
portal_domain="glasswall.example.com"
keycloak_domain="keycloak.example.com"
helm upgrade --install cdrplatform-portal-access ./cdrplatform-portal-access \
--set image.tag="${image_tag:?}" \
--set image.pullPolicy=IfNotPresent \
--set ingress.tls.domain="${portal_domain:?}" \
--set ingress.tls.enabled=true \
--set ingress.tls.secretName="tls-secret" \
--set configuration.AuthenticationScheme="Bearer" \
--set configuration.Authentication__Schemes__Bearer__ValidAudiences__0="api://cdrplatform-portal-access" \
--set configuration.Authentication__Schemes__Bearer__ValidIssuer="https://${keycloak_domain:?}/realms/glasswall" \
--set configuration.Authentication__Schemes__Bearer__Authority="https://${keycloak_domain:?}/realms/glasswall" \
--set configuration.Authentication__Schemes__Bearer__RequireHttpsMetadata=true \
--set configuration.Authentication__Schemes__Bearer__MetadataAddress="https://${keycloak_domain:?}/realms/glasswall/.well-known/openid-configuration" \
--set configuration.Authentication__Schemes__Bearer__JwksUri="https://${keycloak_domain:?}/realms/glasswall/protocol/openid-connect/certs" \
--atomic
Deploy API-Access
api_access_image_tag=$(k get deploy api-access -o json | jq -r '.spec.template.spec.containers[0].image' | cut -d":" -f2)
portal_domain="test.cdr.glasswall.dev"
keycloak_domain="pbkc.cdr.glasswall.dev"
helm upgrade --install cdrplatform-api-access ./cdrplatform-api-access \
--set image.tag="${api_access_image_tag:?}" \
--set image.pullPolicy=IfNotPresent \
--set ingress.tls.enabled=true \
--set ingress.tls.secretName="tls-secret" \
--set ingress.tls.domain="${portal_domain:?}" \
--set configuration.AuthenticationScheme="Bearer" \
--set configuration.Authentication__Schemes__Bearer__ValidAudiences__0="api://cdrplatform-api-access" \
--set configuration.Authentication__Schemes__Bearer__ValidIssuer="https://${keycloak_domain:?}/realms/glasswall" \
--set configuration.Authentication__Schemes__Bearer__Authority="https://${keycloak_domain:?}/realms/glasswall" \
--set configuration.Authentication__Schemes__Bearer__RequireHttpsMetadata=true \
--set configuration.Authentication__Schemes__Bearer__MetadataAddress="https://${keycloak_domain:?}/realms/glasswall/.well-known/openid-configuration" \
--set configuration.Authentication__Schemes__Bearer__JwksUri="https://${keycloak_domain:?}/realms/glasswall/protocol/openid-connect/certs" \
--atomic
3.1 Post-deployment checklist
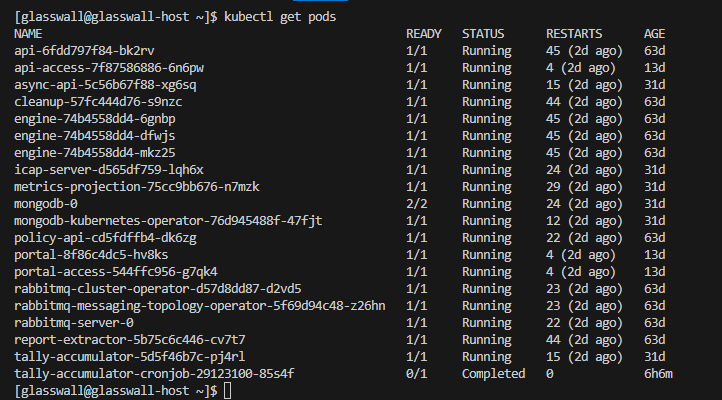
- Ensure that the pods are running (no
CrashLoopBackOff). - Also check that the logs show successful Keycloak OIDC config.
Step 4 - Validation and testing SSO Integration
4.1 Browser login test
a. Launch the Halo portal.
b. Get redirected to Keycloak login.
c. Sign in to your account.
d. Return to Halo after being authenticated.
Step 5 - Troubleshooting
Misconfigured redirect URI
Check URIs match between portal and Keycloak.
Clock skew
Sync system clocks.
TLS trust errors
Ensure Halo trusts Keycloak’s cert.