The Halo Portal gives users the opportunity to explore and experience Glasswall’s advanced Content Disarm and Reconstruction (CDR) technology first-hand. Through the Clean a file tool, users can easily upload and sanitize files using an intuitive, user-friendly interface. This demo tool provides a fast and reliable way to remove hidden threats that traditional antivirus solutions often miss, ensuring files are safe to open and share.
During the file sanitization process, Glasswall Halo deconstructs each file into its individual components and examines its underlying structure; often referred to as its digital DNA. Any elements that deviate from the file’s original manufacturer specifications or pose potential security risks are removed. The file is then meticulously rebuilt to its intended format, producing a clean, secure, and visually identical version that preserves usability while eliminating malicious content.
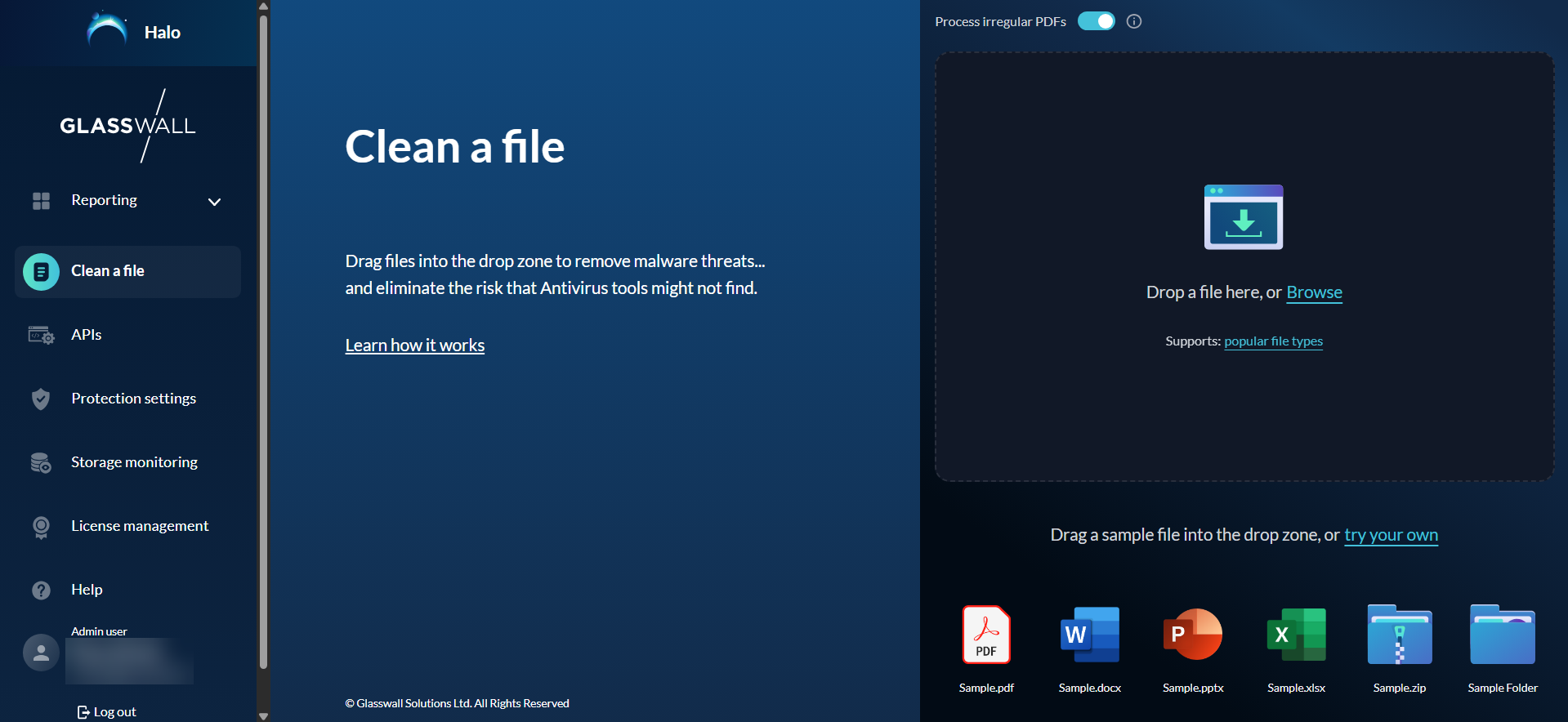
What would you like to do?
Clean a file
Glasswall Halo's file cleaning application allows you to input files in two ways, as explained below.
Drag and drop
The quicker and more intuitive way of using this application simply involves dragging and dropping your required file into the Drop Zone area.
- The file is then instantly processed, rebuilt, and made available for download.
- A detailed report of the file changes is also created for your reference.
Upload a file
Users can also input files via a simple upload process.
- Click Browse from the Drop Zone area and select a file from your device.
- Halo will then process the file and rebuild it to its 'known good' standards.
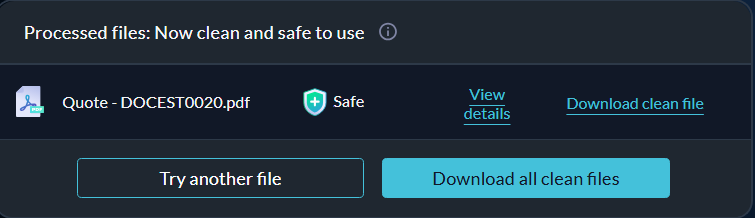
View details
After your file has been processed and rebuilt by Halo, a summary of the changes made is compiled for your reference.
To find out how Glasswall made your file safe, click View details.
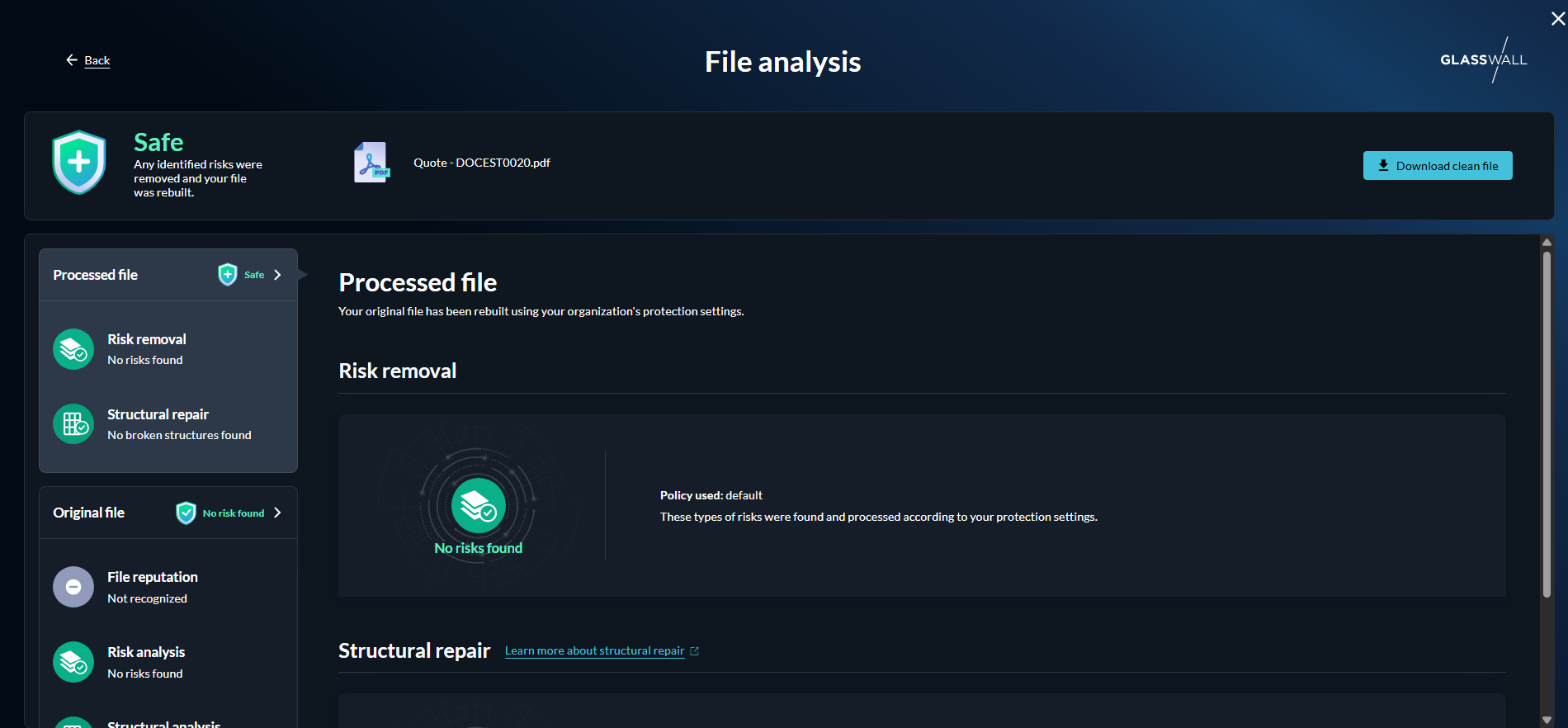
This will display the Original file risk level along with a description of what it means.
File analysis
The system breaks the file down into its core components, examining its structure, content, and potential threats. Once processing is complete, the* File analysis* view provides a detailed technical breakdown of what was discovered and the actions taken to secure the file.
This includes information on any content that was removed during sanitization, the file’s reputation as assessed by ReversingLabs, a comprehensive risk analysis highlighting potential vulnerabilities, and details of any structural repairs applied to restore the file to a safe, functional state. By presenting this level of detail, users gain full visibility into the protection process, allowing them to understand exactly how the file was cleaned and reinforced while maintaining its original usability.
Download a cleaned file
Once Halo has processed your file, the rebuilt clean file will be made available to you for download.
Click Download clean file and save it to your device.
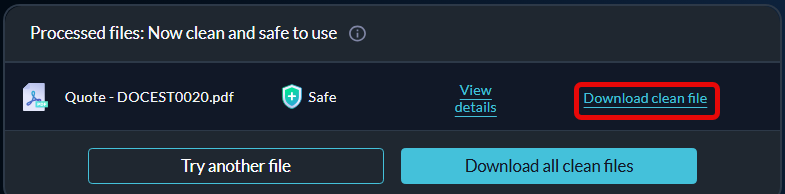
Alternatively, if you processed an entire folder of files at once, you could download the sanitized files together by clicking Download all clean files.
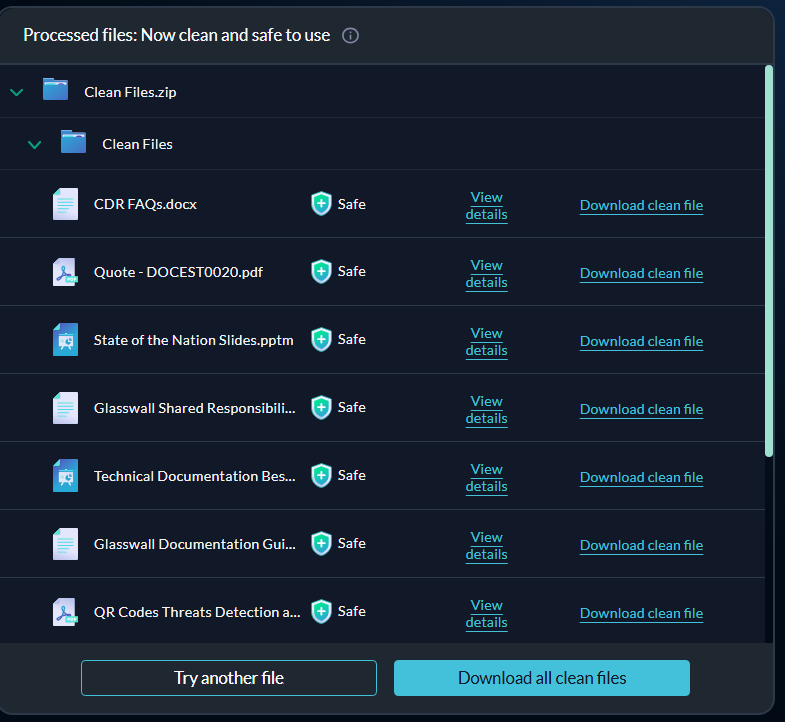
Clean and download multiple files
Users can sanitize not just individual files but also multiple files or entire folders in a single, streamlined process.
There are two ways to do this: either select the files you want to process using the upload option or drag and drop an entire folder into the Drop Zone.
Note: you can process up to 100 files at a time.
Once processing is complete, all sanitized files can be downloaded together by clicking Download all clean files. For a deeper understanding of what was done to each file, you can view detailed analysis information for individual files by selecting View details.
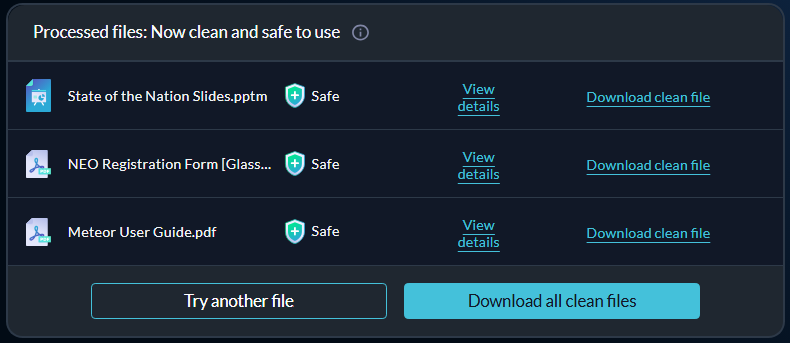
Clean archive files
Archive files are quite often used as a quicker and easier way to transfer multiple files. For this reason, we have enabled Halo to process archive files and folders to ensure enterprise users can quickly check if a large number of incoming or outgoing files are a threat.
You can process archive files in the same way as a single file, by either uploading the archive folder or dragging and dropping the folder into the Drop Zone. Clean Room can process an archive that contains folders and files inside, but not other archives.
Once the files have been cleaned, you can download each file individually or altogether by clicking Download all clean files.